
Winbond’s Secure Flash Memory Technology—a Deep Dive
Embedded security rank stands out as one of the most critical technology areas for semiconductor memory.
For embedded security, Winbond has a product line called TrustME secure flash memory. These devices feature sophisticated logic built directly into the hardware of the flash devices. This provides the separate layer needed to handle the resiliency demands of standards such as NIST SP800-193.
In this article, we take a deep dive into this technology and examine the problems it solves for engineers developing systems requiring advanced embedded security.
At electronica 2024, All About Circuits' Editor-in-Chief discusses memory technologies with Teck Hwee Lim, Sales Division Director at Winbond.
Winbond’s TrustME Secure Flash Memory
In March of 2024, Winbond introduced an expansion of its TrustME Secure Flash W77Q family with 256 Mb, 512 Mb, and 1 Gb chips. Significantly, these devices were the first to implement the Leighton–Micali Signature (LMS) algorithm for PQC (Post Quantum Cryptography). PQC is a critical enhancement for securing connected IoT edge devices used in commercial, industrial, and server segments.
The W77Q devices provide a number of key security features, including:
- Code and Data Protection—Root-of-Trust implementation follows the TCG DICE attestation mechanism.
- Authentication—Stringent authentication protocols, ensuring that only authorized actors and software layers gain access.
- Secure Software Updates with Rollback Protection—Employs Leighton-Micali Signature (LMS) algorithms, as recommended by NIST Special Publication 800-208.
- Platform Resiliency—Follows NIST 800-193 recommendations, meaning that unauthorized code changes are automatically detected, enabling the system to recover to a secure state and disturbing potential cyber threats.
- Secure Supply Chain—The origin and integrity of flash content are guaranteed by Secure Flash at every stage of the supply chain. W77Q implements remote attestation based on LMS-OTS (NIST 800-208).
While all these security measures are important, for this deep dive, we will focus on the critical topic of the NIST-800-193 standard recommendations and how they ensure platform resiliency.
The NIST 800-193 Standard and Platform Resiliency
The origin of NIST-800-193 is tied closely with the emergence of the Internet of Things (IoT) phenomenon around 20 years ago. The idea envisioned that every system or appliance would be smart and have some internet connectivity that would serve some advanced features. But back then, cybersecurity was only thought about in conjunction with computers and servers, and not the “things” part of IoT.
As these connected IoT devices evolved, they became a part of many segments of the modern world, including infrastructure, utilities, households, and government agencies. This drove the US agency National Institute for Standards in Technology (NIST) to publish its NIST SP800-193 “Platform Firmware Resiliency Guidelines” in May 2018.
The publication targets every connected device which runs any sort of firmware—from large and complex servers and all the way to small and embedded controllers. This publication and its principles will be explored here.
Three Pillars of Resiliency
NIST SP800-193 discusses the concept of “resiliency.” In this context, that means making a system or platform resistant to malfunction due to malicious attacks or spontaneous errors. You can look at resiliency as being composed of three pillars: protect, detect, and recover.
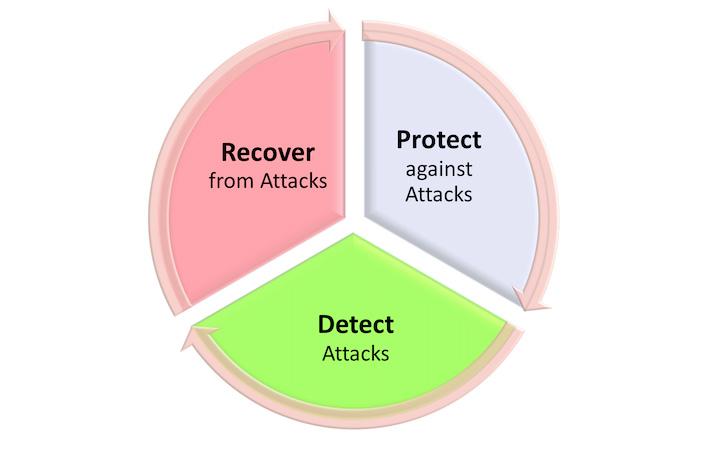
Winbond’s TrustME Secure Flash provides the means to protect-against, detect, and recover-from unauthorized changes of code and critical data stored in the flash memory.
Protection is all about ensuring that platform code and data remain in a state of integrity. Detection is the capability of the platform to identify and alert corruption to code and critical data. Recovery is the capability of the system to return to a correct working state in terms of code and critical data. Note that SP800-193 only covers the resiliency of firmware and critical data. It does not cover loss or corruption of other data or any hardware or physical damage to the system.
How Winbond’s Secure Flash Meets NIST SP800-193
Winbond’s family of TrustME secure flash devices are designed with resiliency at their core. They address the three pillars of SP800-193. Let’s take each pillar one by one.
Protection
Root of Trust—Keeping the firmware in a state of integrity allows it to be trusted, known as “Root of Trust.” The user and infrastructure can rely on the functionality of the firmware to correctly operate the system and verify the authenticity and integrity of other parts of the firmware before executing them.
Cryptographic Write Protection—To handle protection and keep the system firmware and critical data in a state of integrity, Winbond Secure Flash devices employ cryptographic write protection (CWP). CWP allows the platform designer to protect sections of the flash device from erase or program operations.
Authenticated Update Mechanism—SP800-193 requires that the system firmware be updated in a timely manner to patch security vulnerabilities. SP800-193 requires that the update is done via an authenticated update mechanism, ensuring that the update is authentic (true to source) and integral (complete and unmodified). Winbond Secure Flash includes a built-in mechanism to provide firmware updates with authentication and integrity protection. On top of these, the update mechanism provides roll-back protection and atomic operation.
Detection
SP800-193 requires that the system detects unauthorized changes to firmware and critical data before it is executed or used. Upon detection, the system may initiate a recovery process.
Automatic Integrity Check—Winbond’s Secure Flash initiates an automatic integrity check to the firmware section upon power-up and as requested by the user. This integrity check scans the entire firmware section, looking for any unauthorized changes. If unauthorized changes are detected, the secure flash implements a recovery process described below. The automatic integrity check is fully implemented in the flash hardware and, therefore, provides an additional, separate layer of protection.
Firmware Initiated Data Authentication—To authenticate critical data, Winbond’s Secure Flash supports a dedicated hardware-based authentication mechanism. This mechanism can be initiated at will by firmware to ensure critical data has not been corrupted. The mechanism is based on a built-in SHA-256 engine. It allows ultra-fast authentication of large data sets without having to move the data from flash into memory.
Recovery
A recovery mechanism should restore the platform firmware and critical data to a valid and authorized state when it is detected to have been corrupted.
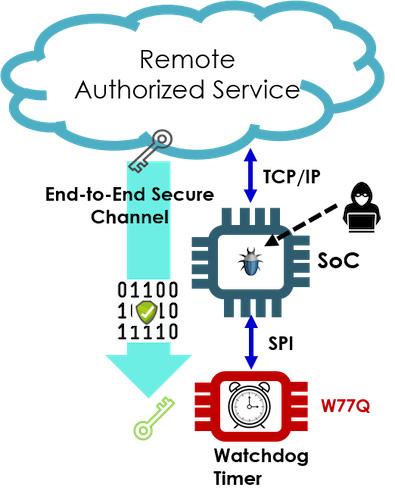
Winbond Secure Flash automatically and authentically recovers platform firmware to a state of integrity in the event that any such firmware code or critical data are detected to have been corrupted or hacked.
Automatic Firmware Fallback—To support automatic firmware recovery, Winbond Secure Flash devices allocate a fallback section. This section contains alternative firmware that is automatically swapped for the corrupted firmware when corruption is detected. The automatic firmware fallback works in conjunction with the automatic integrity check. During system power-on the firmware integrity is checked internally by the flash.
The fallback firmware is protected by cryptographic write protection using a unique key dedicated to that section. That means that compromising the keys to other sections does not compromise the fallback firmware. This addresses the requirements of SP800-193 for the integrity of the recovery mechanism.
Recovery Of Critical Data—Winbond’s Secure Flash allows for various protection schemes for each section. Critical data can be saved in two separate sections, each with a unique key, allowing for critical data protection from corruption or malicious attacks. A safe copy of the data can, therefore, be kept locally in a protected manner and used in case of data corruption.
More details about Winbond’s technology are available at the company’s Secure Flash page.
A Key Asset for Nex-Gen Designs
Technologies like Winbond’s Secure Flash family are key assets for next-gen system designs. To learn more, be sure to check out Winbond’s website. And, if you’re in Munich, Germany this week, please visit Winbond at its booth A5-153 at the Electronica 2024 trade fair.


